How to Use CommandHound to Actually Complete Your COBIT 5 Checklist
Corporations are constantly threatened by information security breaches. Learn how to effectively execute a comprehensive information security strategy.
 IT Security Becomes Easier When Companies Drive a Culture of Accountability
IT Security Becomes Easier When Companies Drive a Culture of Accountability
As online information becomes increasingly more difficult to protect and easier for hackers to access, companies are forced to face the reality that their internal information security systems might not be comprehensive enough. Luckily, corporations are not alone when trying to develop comprehensive programs to ensure nothing is forgotten.
International organizations like ISACA and ISO have worked for years to develop frameworks for companies to use when developing and managing technology. Both the COBIT 5 and ISO-27001 are valuable frameworks for corporations interested in maintaining the most up-to-date IT management and operational standards in order to protect their sensitive data. But both of these frameworks include hundreds of tasks that have to be completed on a regular basis.
Every IT professional knows the serious consequences that can come to pass if an employee becomes a COBIT or ISO 27001 liability or if compliance with these frameworks is not a top priority, but actually making sure that all of the hundreds of tasks that need to get done are completed is another headache altogether.
Now that you know How CommandHound Works to Instill a Culture of Accountability in the Workplace, our 8 Tips for a Smooth ISO Certification, and how to Solve the Top Challenge of Implementing COBIT 5, you’re probably curious to learn more about how to actually use CommandHound to drive the required accountability to make sure things get done.
That’s why we’ve created this easy step-by-step guide to help you set up an information security compliance process using the CommandHound platform. In this example, we’ll be using the COBIT framework, but using CommandHound for any other framework works just as well.
Step 1: Input COBIT 5 Tasks into CommandHound
The Internet is full of COBIT checklists that make it easy to know what specific Control Points (i.e., tasks) need to be done to maintain COBIT compliance. At CommandHound, we have found that the easiest way to group Control Points is by the 4 sections of the COBIT framework.
Start by making a Control Tower for each of the 4 standard groups:
- Plan and Organize
- Acquire and Implement
- Deliver and Support
- Monitor and Evaluate
You can then input all of the Control Points, or the critical tasks that need to be monitored and completed, into each of these groups. With COBIT, these include the 34 processes that align with the responsibility areas of plan, build, run, and monitor into each of these groups. By creating a Control Point for each of the tasks, you can then group them in whatever way seems best for your team (as you see in the photo below).
CommandHound even allows you to create Templates from your Control Towers (as shown in these images). This means that your COBIT Control Towers are saved in the system for whenever you want to reuse them. Next time your COBIT process starts, simply use one of your Templates to recreate all of your Control Towers and Control Points. This will save you both time and effort.
Step 2: Set Deadlines and Escalation Routes for Tasks
This is where using CommandHound allows you to hold teams more accountable than simple checklists or task management systems. After inputting all of the Control Points, or specific tasks necessary for COBIT 5 compliance, you can assign each of them to a specific individual on your team, set due dates, and designate who will be notified and escalated to if that task is not completed on time as expected.
These escalation paths ensure that nothing will be forgotten or allowed to slip through the cracks. When a task is escalated, its status changes from green to yellow or red depending on the urgency and drives higher levels in the organization to step in if necessary to make sure things get done.
Step 3: Track Performance and Monitor Tasks
Over time, CommandHound will track your COBIT tasks and their completion, making sure that nothing is left out and that no individual team member allows crucial tasks to slip through the cracks. CommandHound’s detailed and easy-to-use metrics record team members’ task completion performance for later analysis and performance review purposes.
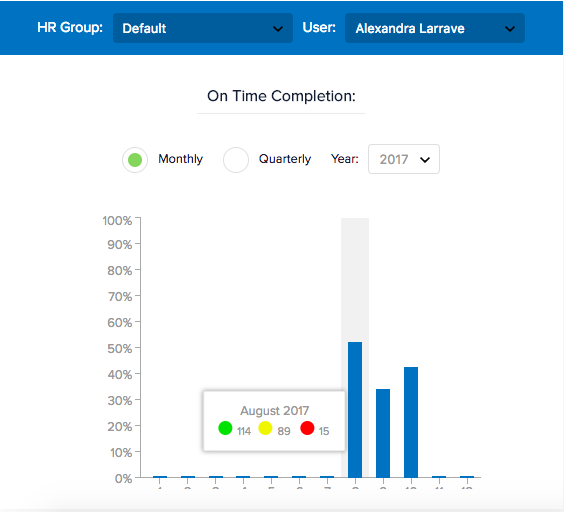 CommandHound’s Metrics Track Completion and Performance By Individual To Drive Accountability
CommandHound’s Metrics Track Completion and Performance By Individual To Drive AccountabilityWith CommandHound, teams are able to delegate tasks, monitor their upcoming deadlines, and escalate these tasks when they are not completed in time. When team members know that their task completion is being tracked, a culture of accountability quickly develops that keeps your organization fully COBIT compliant.
Accountability and COBIT compliance go hand in hand, and CommandHound helps you develop the culture of accountability that will keep your organization following the COBIT 5 framework at all times. Learn more by signing up for a free 15-minute demo today:
